Amid the rise of cyberwarfare and hacktivism driven by geopolitical events, a series of malicious cyberattacks has reversed trends, according to the 10th Threat Landscape Report published by the European Union Cybersecurity Agency (ENISA).
With over 10 terabytes of data being stolen every month, ransomware (Ed.: a type of malware that threatens to reveal a victim’s personal data or block access to it until a ransom is paid) is still considered one of the top threats.
The report covers the period from July 2021 to July 2022
The most common method of cyber attacks is recognized phishingone. This list also includes “distributed attacks” such as “denial of service” (DDoS2). Geopolitical events, especially Russia’s invasion of Ukraine, served as a catalyst for the development of the cyber sphere. While we continue to see an increase in the number of threats, we are also seeing the emergence of a wider range of methods such as zero-day exploits (used by hackers to attack systems with a vulnerability that has not been identified before), AI-assisted misinformation, and deep forgery (a person in an existing image or the video is replaced by another). As a result, more malicious and large-scale attacks with more destructive consequences have appeared.
Juan LePasaar, executive director of the agency, said: “The current global context is inevitably leading to significant changes in the scope of cybersecurity threats. A new paradigm is being shaped by a wide range of threats. We are entering a phase where we will need appropriate strategies to protect all of our critical sectors, our industrial partners and therefore all citizens EU“.
Main threat factors and their analysis
State-sponsored hackers, cybercrime, hired hackers and hacktivists remain the most significant threat actors. Based on an analysis of the proximity of cyber threats to the European Union (EU), the number of incidents remains high during the reporting period in the NEAR category. This category includes affected networks and systems within the EU. It also covers populations that have been attacked within the borders of the European Union.
The breakdown of threats by sector is an important aspect of the report, as it shows that no one was left unaffected. The report shows that almost 50% of threats target the following categories: public administration and governments (24%), digital service providers (13%), the general public (12%). The other half is distributed among all other sectors of the economy.
Main Threats
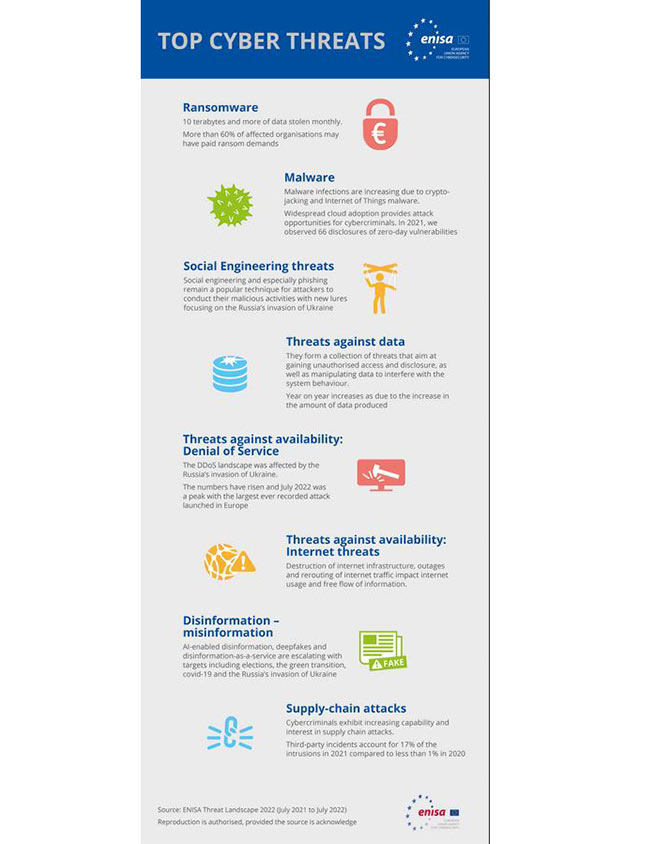
ENISA divided the threats into 8 groups. Frequency and impact determine how noticeable they are still:
- Ransomware:
- 60% of the affected organizations could demand a ransom.
- Malware:
- 66 zero-day disclosures in 2021.
- Social engineering:
- Phishing remains a popular method, but we are seeing the emergence of new forms of phishing such as spear phishing, whaling, smishing and vishing.
- Threats against data:
- The increase is proportional to the total amount of data produced.
- Accessibility Threats:
- The largest denial of service (DDoS) attack was launched in Europe in July 2022;
- Internet: destruction of infrastructure, interruptions in work and redirection of Internet traffic.
- Disinformation:
- Escalating disinformation with AI, deepfakes and disinformation as a service.
- Supply chain targeting:
- Third-party incidents account for 17% of intrusions in 2021, compared to less than 1% in 2020.
Contextual trends are emerging. Zero day exploits3 is a new way that attackers use to achieve their goals.
After the outbreak of war between Russia and Ukraine, a new wave of hacktivism. DDoS attacks are becoming larger and more complex, aimed at mobile networks and the Internet in general.
Disinformation with the help of AI and deepfakes: the spread of bots can easily disrupt the norm as well as community interaction by flooding public services with fake content and comments.
Digital Impact
The impact is divided into five parts. ANDVictims of attacks are at risk of potential exposure in the following areas:reputational, digital, financial, physical and social. However, in most cases, the consequences remain unknown because the victims do not provide information or it remains incomplete.
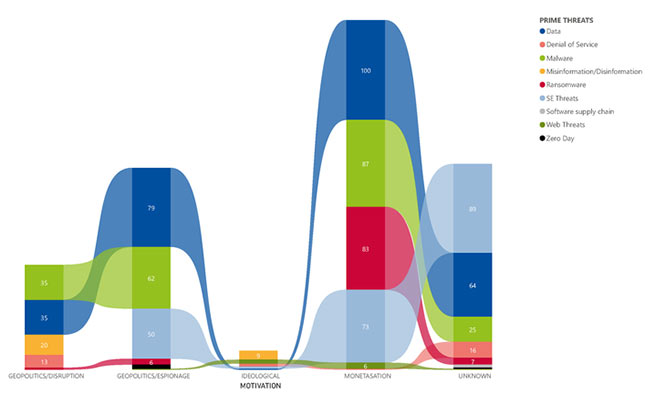
The main threats based on motivation
Ransomware is motivated solely by financial gain. The motivation of state-sponsored groups may be driven by geopolitics. Ideology can also be the driving force behind hacktivist cyber operations.
Stimulation and training of hackers by states parties to the conflict
Against the backdrop of ongoing fighting in Ukraine, hacktivists (hacker activists) are waging their war on the digital front. Russian and Belarusian public services, pages of state media, banking systems and systems of key infrastructures of the countries participating in hostilities fell under the attacks. In Russia and Belarus, such actions of hackers are equated with terrorism and treason, but in Ukraine, join the IT army calls Minister of Digital Transformation, posting instructions and targets for cyberattacks on a telegram channel with over 300,000 subscribers. The almost instantaneous transition of a conventional war between the two countries into an all-out war in which “everything is possible” was somewhat unexpected even for Western countries, and even more so for Russia.
One of the most dangerous trends in this war is the massive use of the civilian population for hacker attacks against the enemy – Russia. But the problem is not even in the attacks themselves, but in the fact that now almost anyone can get their hands on powerful tools created both by professionals working for the state structures of Ukraine and transferred to them from Western allies for hacker attacks. The authors of the instructions insist that any harm to Russia is a benefit to Ukraine. At the same time, participants are convinced that they should not have any moral and ethical restrictions in this activity. Whether it’s a kindergarten or a hospital power supply system, because there is an all-out war in which EVERYTHING is allowed.
For Europe and other countries of the world, the emergence of such a large group of hackers extremely dangerousbecause Not everyone newly minted hackers use this knowledge to fight Russia, and immediately try to make money on easier, from their point of view, goals – commercial companies and individuals in the European Union and the United States. Moreover, the owners of websites and Telegram channels, where instructions and tools for hacking are located, do not restrict their use in any way.
In many countries, the so-called. The collective West does not yet understand how dangerous this phenomenon can be. Indeed, in terms of their danger, these resources are comparable to the smuggling of heavy weapons, fissile materials or bacteriological weapons. The wave of phishing messages that swept this year with the transition to fake sites of Greek banks and the site of the Greek tax system is an example of this.
Without drastic security measures, the Internet structure of the so-called. the digital state of Western countries could be destroyed or disabled, leading to chaos and huge financial losses.
Outcome
The ETL Report maps the cyber threat landscape to help decision makers—politicians and security professionals—determine strategies to protect citizens, organizations, and cyberspace. This work is part of the EU Cybersecurity Agency’s annual work program to provide strategic information to stakeholders. The content of the report is compiled from open sources such as media articles, expert opinions, intelligence reports, incident analysis and security research reports, as well as through interviews with members of the ENISA Cyber Threat Landscapes working group (working group CTL ).
ENISA’s analysis and views on the threat landscape should be industry and vendor neutral. Information based on OSINT (Open Source Information) and ENISA’s work on situational awareness also helped to document the analysis presented in the report.
Additional Information:
- ENISA 2022 Threat Landscape – Infographic
- ENISA Threat Landscape Report 2022
- ENISA Threat Landscape Report 2021
- ENISA Threat Landscape Supply Chain
- ENISA Threat Landscape for Ransomware Attacks – May 2021 – June 2022
Reference
one. Phishing (English phishing, from fishing – fishing, fishing, and password – password) – a type of Internet fraud, the purpose of which is to obtain user identification data. This includes the theft of passwords, credit card numbers, bank accounts, and other sensitive information. Phishing is fake email notifications from banks, providers, payment systems and other organizations that for some reason the recipient urgently needs to transfer/update personal data. The reasons may be various. This may be data loss, system failure, and so on.
2. DDoS (attack) (from the English Distributed Denial of Service – a distributed denial of service attack) – a hacker attack on a computer system in order to bring it to failure, that is, the creation of such conditions under which conscientious users of the system will not be able to access the provided system resources (servers) or this access will be difficult. The failure of the “enemy” system can also be a step towards mastering the system (if in an emergency the software gives out any critical information – for example, version, part of the program code, etc.). But more often it is a measure of economic pressure: the loss of a simple service that generates income, bills from the provider, and measures to avoid the attack significantly hit the target’s pocket. Currently, DDoS attacks are the most popular, as they allow you to bring almost any poorly written system to failure, leaving no legally significant evidence.
3. Zero day exploit – an exploit that was written to exploit a vulnerability that the developer does not yet know about (and, accordingly, there are no patches that fix it). An attacker could exploit this vulnerability if the victim’s computer does not have proactive exploit protection technologies implemented.
four. deepfake (deepfake, concatenation, English deep learning – “deep learning” and fake – “fake”) – an image synthesis technique based on artificial intelligence. The technique is used to connect and superimpose existing images and videos on the original ones. In the vast majority of cases, Generative Adversarial Neural Networks (GANs) are used to create such videos. One part of the algorithm learns from real photographs of a certain object and creates an image, literally “competing” with the second part of the algorithm until it starts to confuse a copy with the original.






More Stories
Association of Professional Nutritionists to be created in Greece
The first ever Miss Artificial Intelligence beauty contest has been announced.
100-year-old Greek woman undergoes heart surgery